Isn’t it absurd to want to protect everything in the same way?
One of the key principles in the field of security is to protect the asset (application, data, server, or any other IT resource) based on its value is fundamental.
This principle is based on the idea that not all resources have the same importance or value to a company, and therefore, do not require the same level of protection.
In the Nuabee solution, we have developed a level of protection adapted to the criticality of your applications and assets.
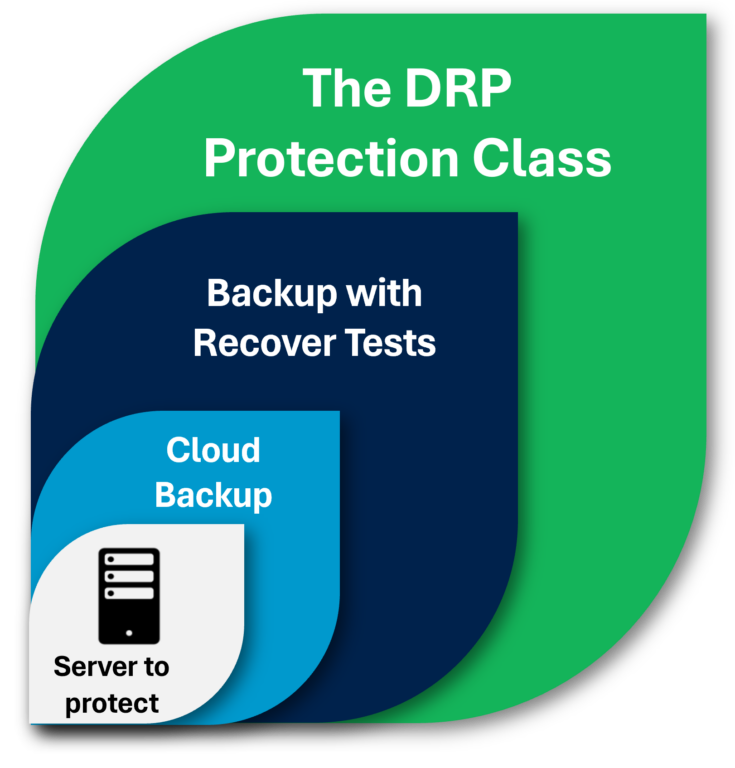
Les 3 classes de protection de la solution Nuabee
Servers in Cloud DRP protection |
Servers in backup with Cloud recover tests |
Servers in simple cloud backup |
The DRP class:This concerns the most critical servers for the company, therefore supporting the most important business applications for the company’s cyber resilience, which are tested regularly (by default every 6 months) in the context of a comprehensive IT disaster recovery test. The main objective is to verify the proper functioning of the servers within the DRP scope. Company users are responsible for checking that the applications work well and that all data is present. This IT disaster recovery test can integrate network tests and tests for reconnecting users to the disaster recovery site. |
The Backup class with Recover Tests:This involves servers that support important applications in the company but do not need to be restarted within 4 or 8 hours following a disaster, but within a few days after activating the DRP. Backups of servers in this class are automatically tested every 6 months (by default) in the Cloud. The startup test is validated through a network port scan and a screenshot of the login page. In case of a disaster, these servers can easily be added to the DRP scope. |
The Outsourced Backup class:This involves servers and applications for which data must be protected in case of a cyberattack. These data may be test data, security data, etc. The data is important and must absolutely be protected (as in the other two classes), but the ability to restart the server is not crucial. This involves servers whose backup (data and OS) is outsourced to the Cloud, and whose isolation from the source information system is essential. |
To provide the best experiences, we use technologies such as cookies to store and/or access device information. Consenting to these technologies will allow us to process data such as browsing behavior or unique IDs on this site. Failure to consent or withdrawing consent may negatively impact certain features and functions.
